初学者 Linux tcpdump 命令教程(8 个示例)
在此页
- Linux tcpdump 命令
- Q1。如何使用 tcpdump?
- Q2。如何让tcpdump在收到一定数量的数据包后退出?
- Q3。如何使 tcpdump 在输出中显示链接级标头?
- Q4。如何让 tcpdump 以数字方式显示外国 IP 地址?
- Q5。如何让 tcpdump 在输出中产生包号?
- Q6。如何使 tcpdump 打印更短的输出?
- Q7。如何从 tcpdump 输出中省略时间戳信息?
- Q8。如何使 tcpdump 产生详细的输出?
- 结论
每次您在计算机上打开网页时,都会在您的网络接口上发送和接收数据包。有时,出于多种原因,分析这些数据包变得很重要。值得庆幸的是,Linux 提供了一个命令行实用程序,可以在输出中转储与这些数据包相关的信息。
在本文中,我们将讨论相关工具 - tcpdump 的基础知识。但在我们这样做之前,值得一提的是,这里的所有示例都已经在 Ubuntu 18.04 LTS 机器和 Debian 10 上进行了测试,但它也适用于其他 Linux 发行版,如 CentOS、Fedora、Gentoo 和 Arch Linux。
Linux tcpdump 命令
Linux 中的 tcpdump 命令可让您转储网络上的流量。以下是它的简短语法:
tcpdump [OPTIONS]下面是详细的语法:
tcpdump [ -AbdDefhHIJKlLnNOpqStuUvxX# ] [ -B buffer_size ]
[ -c count ]
[ -C file_size ] [ -G rotate_seconds ] [ -F file ]
[ -i interface ] [ -j tstamp_type ] [ -m module ] [ -M secret ]
[ --number ] [ -Q in|out|inout ]
[ -r file ] [ -V file ] [ -s snaplen ] [ -T type ] [ -w file ]
[ -W filecount ]
[ -E algo:secret,... ]
[ -y datalinktype ] [ -z postrotate-command ] [ -Z user ]
[ --time-stamp-precision=tstamp_precision ]
[ --immediate-mode ] [ --version ]
[ expression ]以下是工具手册页对其的解释:
Tcpdump prints out a description of the contents of packets on a network interface that match the
boolean expression; the description is preceded by a time stamp, printed, by default, as hours,
minutes, seconds, and fractions of a second since midnight.
It can also be run with the -w flag, which causes it to save the packet data to a file for
later analysis, and/or with the -r flag, which causes it to read from a saved packet file rather
than to read packets from a network interface. It can also be run with the -V flag, which causes
it to read a list of saved packet files.
In all cases, only packets that match expression will be processed by tcpdump.以下是一些 Q&A 风格的示例,可以让您更好地了解 tcpdump 命令的工作原理。
Q1。如何使用 tcpdump?
在使用 tcpdump 嗅探数据包之前,您最好知道您希望该工具在哪个网络接口上工作。要获取系统上可用的网络接口列表,请将 -D 命令行选项与 tcpdump 结合使用。
tcpdump -D以下是手册页解释此选项的方式:
Print the list of the network interfaces available on the system and on which tcpdump can capture
packets. For each network interface, a number and an interface name, possibly followed by a text
description of the interface, is printed. The interface name or the number can be supplied to the
-i flag to specify an interface on which to capture.
This can be useful on systems that don't have a command to list them (e.g., Windows systems, or
UNIX systems lacking ifconfig -a); the number can be useful on Windows 2000 and later systems,
where the interface name is a somewhat complex string.
The -D flag will not be supported if tcpdump was built with an older version of libpcap that
lacks the pcap_findalldevs() function.例如,在我的例子中,产生了以下输出:
1.wlx18a6f713679b [Up, Running]
2.any (Pseudo-device that captures on all interfaces) [Up, Running]
3.lo [Up, Running, Loopback]
4.enp3s0 [Up]
5.nflog (Linux netfilter log (NFLOG) interface)
6.nfqueue (Linux netfilter queue (NFQUEUE) interface)
7.usbmon1 (USB bus number 1)
8.usbmon2 (USB bus number 2)
9.usbmon3 (USB bus number 3)
10.usbmon4 (USB bus number 4)现在您有了一个接口列表,您可以选择一个,并将其名称作为输入传递给 tcpdump 的 -i 命令行选项。例如:
tcpdump -i wlx18a6f713679b在我的案例中,以下是此命令产生的部分输出:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on wlx18a6f713679b, link-type EN10MB (Ethernet), capture size 262144 bytes
11:53:11.408964 IP 192.168.2.132.52898 > 239.255.255.250.3702: UDP, length 656
11:53:11.409492 IP himanshu.57383 > one.one.one.one.domain: 8572+ [1au] PTR? 250.255.255.239.in-addr.arpa. (57)
11:53:11.409588 IP 192.168.2.140.49690 > 239.255.255.250.1900: UDP, length 174
11:53:11.409954 IP 192.168.2.147.mdns > 224.0.0.251.mdns: 1 [2q] PTR (QU)? _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local. PTR (QU)? _googlecast._tcp.local. (94)
11:53:11.499220 IP one.one.one.one.domain > himanshu.57383: 8572 NXDomain 0/1/1 (114)
11:53:11.499950 IP himanshu.34201 > one.one.one.one.domain: 12068+ [1au] PTR? 132.2.168.192.in-addr.arpa. (55)
11:53:11.591291 IP one.one.one.one.domain > himanshu.34201: 12068 NXDomain* 0/1/2 (278)
11:53:11.592195 IP himanshu.55501 > one.one.one.one.domain: 31630+ [1au] PTR? 1.1.1.1.in-addr.arpa. (49)
11:53:11.842603 IP himanshu.57253 > one.one.one.one.domain: 16905+ [1au] PTR? 140.2.168.192.in-addr.arpa. (55)
11:53:11.951226 IP himanshu.52662 > one.one.one.one.domain: 52377+ [1au] PTR? 251.0.0.224.in-addr.arpa. (53)
11:53:12.428931 IP 192.168.2.140.49690 > 239.255.255.250.1900: UDP, length 174
11:53:12.437905 IP 192.168.2.147.mdns > 224.0.0.251.mdns: 2 [2q] PTR (QM)? _%9E5E7C8F47989526C9BCD95D24084F6F0B27C5ED._sub._googlecast._tcp.local. PTR (QM)? _googlecast._tcp.local. (94)
11:53:12.438730 IP6 fe80::eccc:59f2:fc78:9e07.52899 > ff02::c.3702: UDP, length 656
11:53:12.439017 IP himanshu.33194 > one.one.one.one.domain: 15679+ [1au] PTR? c.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.f.f.ip6.arpa. (101)
11:53:12.572386 IP one.one.one.one.domain > himanshu.33194: 15679 NXDomain 0/1/1 (165)
11:53:12.642129 IP 192.168.2.11.mdns > 224.0.0.251.mdns: 0*- [0q] 1/0/3 PTR Google-Home-Mini-e3a3ae72a03e3d1c60d24653d4666ca6._googlecast._tcp.local. (356)
...
...Q2。如何让tcpdump在收到一定数量的数据包后退出?
这可以使用 -c 命令行选项来实现。例如,如果你希望 tcpdump 只显示 10 个数据包的相关信息,那么你可以通过以下方式实现:
tcpdump -c 10例如,在我的例子中,我执行了以下命令:
tcpdump -c 10 -i wlx18a6f713679b以下是生成的输出:
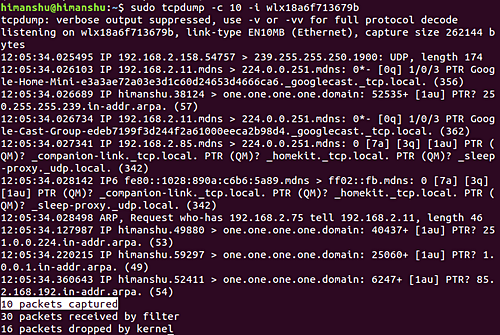
因此您可以看到捕获了 10 个数据包。
Q3.如何使 tcpdump 在输出中显示链接级标头?
这可以使用 -e 命令行选项来完成。例如:
tcpdump -e -i wlx18a6f713679b这是产生的输出:
listening on wlx18a6f713679b, link-type EN10MB (Ethernet), capture size 262144 bytes
12:14:07.951396 3c:a8:2a:a7:7b:c1 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 197: 192.168.2.55.17500 > 255.255.255.255.17500: UDP, length 155
12:14:07.952111 3c:a8:2a:a7:7b:c1 (oui Unknown) > Broadcast, ethertype IPv4 (0x0800), length 197: 192.168.2.55.17500 > 192.168.2.255.17500: UDP, length 155
...
...因此,您可以看到在输出中生成了链接级标头。
Q4.如何让 tcpdump 以数字方式显示外国 IP 地址?
这可以使用 -f 命令行选项来实现。
tcpdump -f -i [INTERFACE]使 tcpdump 以数字方式而非符号方式显示“外国 IPv4 地址”在某些情况下有其优势。工具手册页中提到了一个这样的例子:
this option is intended to get around serious brain damage in Sun's NIS server — usually it hangs
forever translating non-local internet numbersQ5.如何让 tcpdump 在输出中产生包号?
要使 tcpdump 在输出中生成数据包编号,请使用 --number 命令行选项。
例如,我执行了以下命令:
tcpdump --number -i wlx18a6f713679b这是产生的输出的一部分:
listening on wlx18a6f713679b, link-type EN10MB (Ethernet), capture size 262144 bytes
1 12:38:35.522944 ARP, Request who-has 192.168.2.196 tell _gateway, length 46
2 12:38:35.523265 IP6 fe80::8ab4:a6ff:fe9d:a6bb > ff02::16: HBH ICMP6, multicast listener report v2, 1 group record(s), length 28
3 12:38:35.523578 IP6 fe80::8ab4:a6ff:fe9d:a6bb > ip6-allrouters: ICMP6, router solicitation, length 16
4 12:38:35.523861 ARP, Request who-has 192.168.2.15 tell 192.168.2.170, length 28
...
...
...所以你可以看到现在每一行都以一个数字开头。
Q6.如何使 tcpdump 打印更短的输出?
这可以使用 -q 命令行选项来完成。以下是工具手册页对其的解释:
Quick (quiet?) output. Print less protocol information so output lines are shorter.以下是此选项的示例:
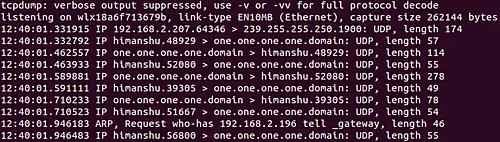
所以你可以看到这次输出中产生的信息较少。
Q7.如何从 tcpdump 输出中省略时间戳信息?
为此使用 -t 命令行选项。这是一个示例命令:
tcpdump -t -i wlx18a6f713679b以下是它的输出:
listening on wlx18a6f713679b, link-type EN10MB (Ethernet), capture size 262144 bytes
IP himanshu.56992 > mails11.telegram.org.https: Flags [.], ack 3090054317, win 965, options [nop,nop,TS val 226976758 ecr 3781653930], length 0
IP himanshu.41122 > one.one.one.one.domain: 12755+ [1au] PTR? 22.171.154.149.in-addr.arpa. (56)
IP mails11.telegram.org.https > himanshu.56824: Flags [.], ack 273652159, win 1001, options [nop,nop,TS val 3781656472 ecr 226966324], length 0
ARP, Request who-has 192.168.2.48 tell _gateway, length 46
ARP, Request who-has 192.168.2.135 tell _gateway, length 46
...
...所以你可以看到时间戳信息(通常在每行的开头)现在不在输出中。
Q8.如何使 tcpdump 产生详细的输出?
在这种情况下,您可以使用 -v 命令行选项。以下是工具手册页如何解释此选项:
tcpdump -v -i [INTERFACE]When parsing and printing, produce (slightly more) verbose output. For example, the time to live,
identification, total length and options in an IP packet are printed. Also enables additional
packet integrity checks such as verifying the IP and ICMP header checksum.
When writing to a file with the -w option, report, every 10 seconds, the number of packets captured结论
由于 tcpdump 命令提供了许多命令行选项,我们在这里只是触及了表面。完成这些练习后,您可以前往工具手册页了解更多信息。
